In this challenge, you're provided with a file that contains reverse engineering challenges, each more difficult than the last.
I downloaded the file onto my instance of Kali Linux and opened a terminal. I used the strings command on the downloaded file:
strings /path/to/your/file
Running strings on a file will normally give you a long output showing non-human readable content towards the top and bottom. The information of value is usually found near the middle of that output. After reviewing the output, I found the following content:
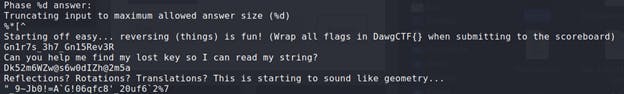
Below "Starting off easy..." there's an alpha numeric string that reads :
Gn1r7s_3h7_Gn15Rev3R
I copied this input and went over to CyberChef. For those who aren't familiar, CyberChef is a browser-based jack-of-all-trades tool developed by the UK's GCHQ (found here ).
I pasted in the string and applied the "Reverse" function in the recipe pane and voila:
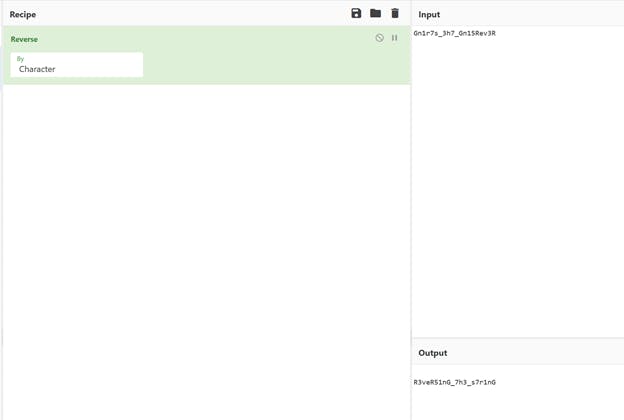
Flag for the challenge:
DawgCTF{R3veR51nG_7h3_s7r1nG}
