Unfortunately there is no rarity in daily news reporting on a new corporate victim of ransomware. The general population is most privy to its impacts because of the effects it has on the supply chain: fuel prices sky rocket, virtual services become unavailable, and in some instances entire city infrastructures are shut down.
Ransomware has taken the cyber world by storm in the last 5-10 years and its prevalence can be tied to a primary reason: its effectiveness. The perpetrators behind ransomware attacks more often than not wind up making profits and sizeable ones at that. This blog post will go into what ransomware is, why it's so effective, and prevention mechanisms that can be put into place to mitigate the risk of experiencing a ransomware attack in a corporate environment.
What is ransomware?
Ransomware is a cyber attack where malicious actors restrict an entity's access to its data and maintain control of it until a payment is made (or as the name implies, hold the data/virtual assets for ransom). Malicious actors or e-criminals can gain access to a network in a variety of ways; these methods typically include:
- Malicious e-mail attachments/phishing: This is one of the most leveraged vectors for malware in general, and ransomware is no exception. E-mail attachments such as Microsoft Office files with malicious macros are a prevalent example of how unsuspecting users unfortunately grant the attackers a foothold on their systems.
- Fake software updates/patches: E-criminals have perfected the art of convincing users that websites and software are legitimate. In the case of Bad Rabbit, for example, users download illegitimate Adobe Flash updates from compromised websites and do not realize that they are actually downloading malware onto their endpoint.
- Drive-by downloads: This is one of the quieter methods elaborated upon in this post, and it occurs when a user visits an infected website and uses an inherently vulnerable app, software program, or web browser. The unsettling aspect of this vector is that it requires no explicit action by the user other than simply using the vulnerable object and accessing the website.
- Self-propagating: Ransomware like WannaCry will replicate itself across a network without a need for human involvement; once the malware gains an initial entry point into the environment, it will spread on its own to other hosts
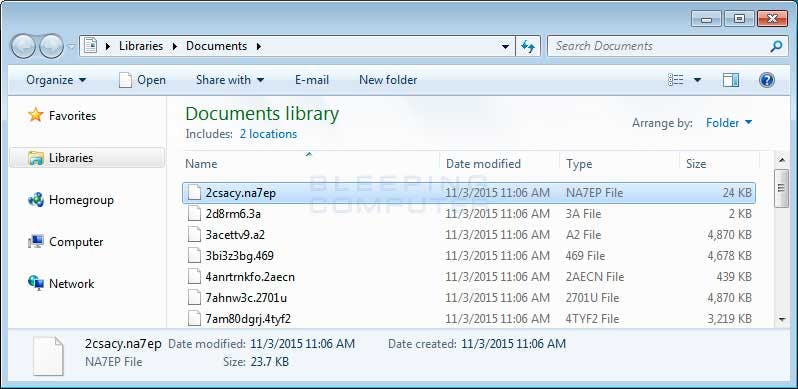
Once the ransomware is on the endpoint, it begins encrypting all files. Ransomware uses a form of what is known as asymmetric public key cryptography. In simple terms, the data is encrypted on the victim computer using a public key and the key required to decrypt the data is a private key only known to the e-criminal/malicious actor. More information on asymmetric cryptography can be found here, here, and here. Below is an example of what the encrypted files would look like on an endpoint affected by Cryptowall ransomware:
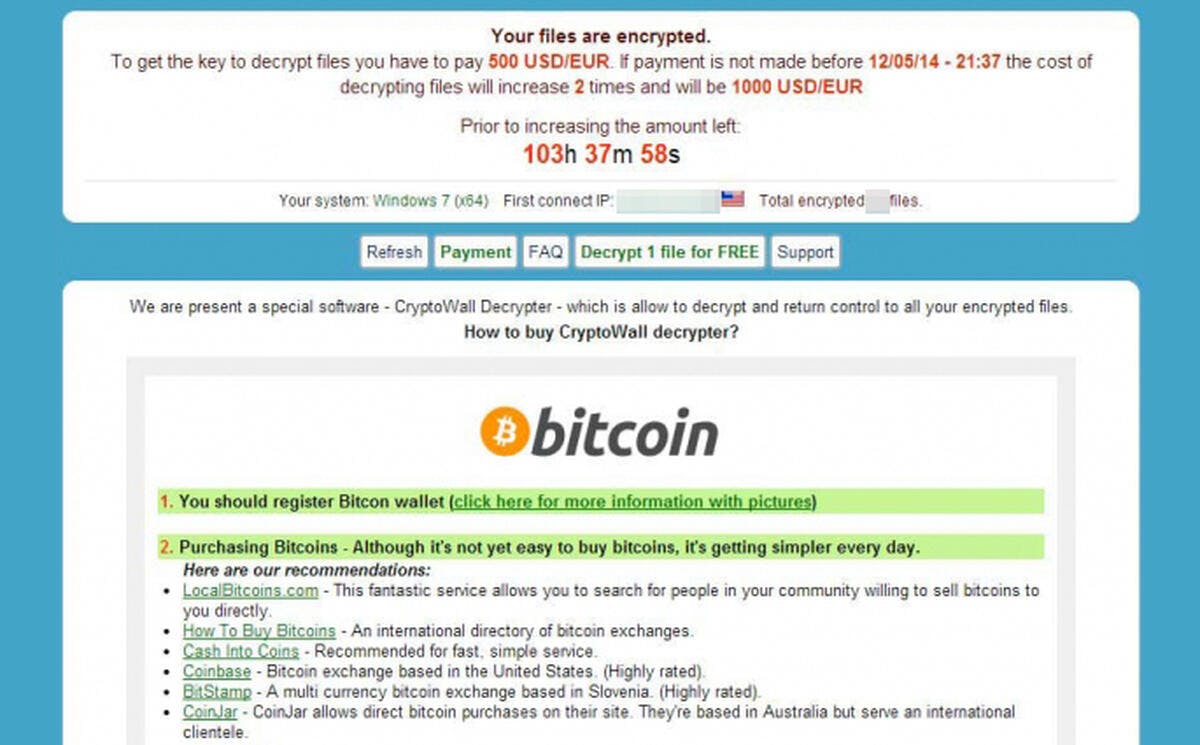
The user is then presented with a message similar to the one pictured below explaining that his/her/their files have been encrypted and are irrecoverable without payment:
Some ransomware, like Gandcrab, goes to the extent of deleting volume shadow copies, ensuring that the victim is unable to restore data from backups.
Why is ransomware so effective?
Ransomware has become the go-to profit mechanism for e-criminals because of its success rate. Malicious cyber actors with enough technical aptitude to develop the malware (or enough money to purchase the implants or solicit ransomware as a service on the black market/dark web) can strategically target corporations in order to extort them for money.
In this strategic targeting, it's not just about going after large, financially successful companies like Amazon, Microsoft, or Tesla, but rather targeting companies that meet a key overlap criteria: companies that manage or distribute key resources and are likely to not possess robust security systems or even maintain security systems up-to-date. Time and time again it has become regrettably evident that the infrastructure behind some of the world's most key resources is not secured with the most up-to-date or cutting-edge security software; sometimes the software used for the actual device functions is simply not even updated or patched with the latest releases.
Why does that overlap of criteria offer e-criminals the most viable means for a successful ransomware attack? Let's start with the latter portion of it: a vulnerable system is just easier to take advantage of. The industrial control systems behind key resources such as oil, electricity, and water treatment, have had a recurring history of being known-vulnerable systems. Couple that with a lack of updates or a lack of security and the compounding effect of vulnerabilities just exponentially increases the adversary attack surface.
The former aspect, the targeting of companies that mange or distribute key resources, gives the attackers a psychological advantage in the attack. Compromising access to key resources or threatening to damage, poison, or irrecoverably destroy key resources elicits panic amongst all stakeholders, especially when a timer is added to the ransom note as seen in the WannaCry ransomware image below:
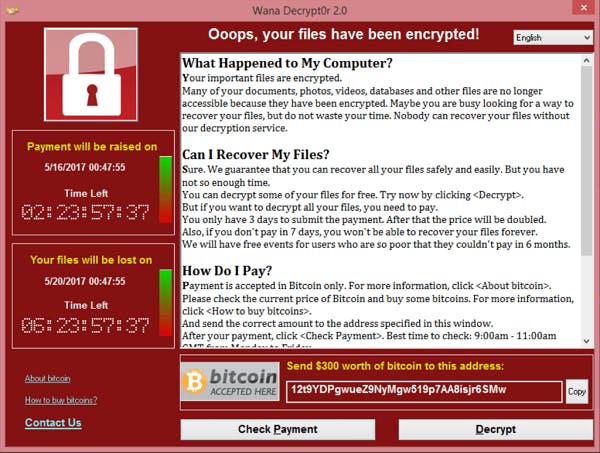
Restricting access to electricity in the middle of winter or altering the chemicals in the purification process at water treatment facility can result in the death of hundreds or thousands of citizens. The more alarming thing is: neither of these specific scenarios is purely conceptual. They've been at minimum "tested" if not already attempted (you can read about them here and here).
The panic instilled in the victims of the attack applies pressure and increases the odds that they will pay the e-criminals rather than risking long-term damage to their resources or services. Some readers may have already considered that these attacks transcend the e-crime realm and go into the geo-political realm, and those readers are correct. As seen in the Crash Override article referenced previously in the post, these mechanisms can absolutely be leveraged for political reasons, but in order to maintain focus on the topic at hand, we will refrain from delving into those theoretics.
It's also important to note that while this article heavily references industrial control systems and key infrastructure of the like, these sectors are not the only targets of ransomware attacks. Places that offer critical services (such as hospitals and healthcare systems) have been subjected to ransomware attacks in the past, such as the attack detailed here which resulted in a death.
How to mitigate the risk of becoming a ransomware attack victim
Theoretically, there is no sure-fire way to block every possible attack vector in an environment; however, there are absolutely ways network administrators and security professionals can reduce the adversary attack surface and mitigate the chances of an attack being successful. Those methods include:
- Downloading software and software updates from legitimate sources
- Educating users on how to handle suspicious e-mails or unexpected activity on their endpoints
- Implementing endpoint protection to prevent malicious code from executing on the host
- Ensuring all hosts/systems in the environment are patched/up-to-date
- Maintaining awareness of the latest ransomware attack mechanisms, how they can impact the organization's environment, and implementing mitigations specific to those potential attacks
- Undergoing a vulnerability assessment to expose security gaps across the network
Notable ransomware
For interested readers, below is a list of articles detailing notable ransomware from recent years:
- Threat spotlight: DarkSide, the ransomware used in the Colonial Pipeline attack
- WannaCry ransomware: Everything you need to know
- 'Petya' ransomware attack: what is it and how can it be stopped?
- Bad Rabbit: Ten things you need to know about the latest ransomware outbreak
- Locky ransomware: Why this menace keeps coming back
- The State of CryptoWall in 2018
- Sodinokibi Ransomware Group Adds Malvertising as Delivery Technique