"Baby RE" is considered to be an intro to reverse engineering CTF-style challenge on Hack the Box. It's ideal for folks who have a limited skillset when it comes to extracting content from programs outside of actually running them.
It starts by providing the following prompt:
Once you download and unzip the file, you're left with an ELF (Executable Link Format) program. You can read more on them here .
We start by attempting to run strings on the file:
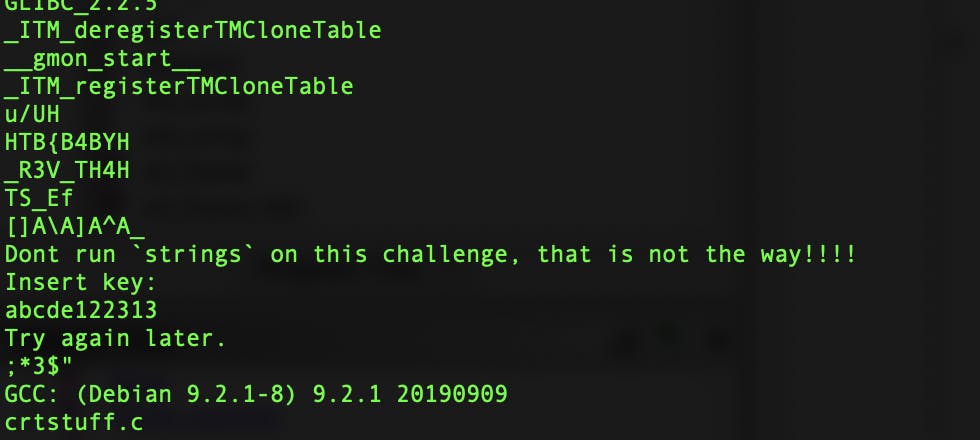
Immediately we can see parts of the flag, but also a comment telling us that strings won't get us the answer. Regardless, it's wise to make a note of the parts of the flag we do see:
HTB{B4BYH
_R3V_TH4H
TS_Ef
Seeing as strings won't work on this challenge, the next step is to throw this file into a debugger. For this challenge, I chose Ghidra. We create a new project and select File -> Import File...
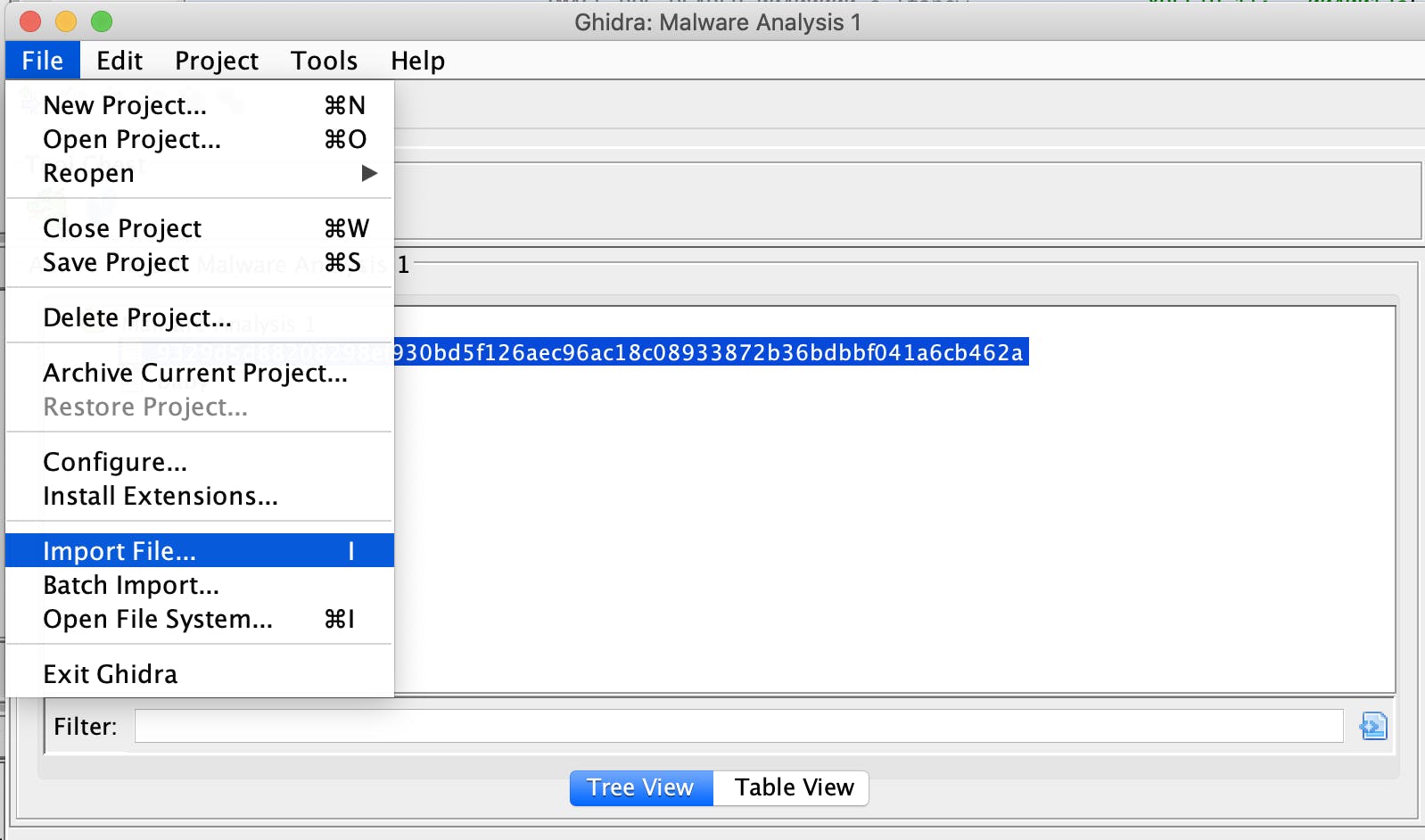
Select "Baby" from the directory you extracted it to, and click Select File To Import. From there, highlight the file and click the icon that looks like this:

This will run Ghidra's "Code Browser." The dragon logo will pop up, but you may still get a blank template that looks like this:
Click File -> Open -> "Baby" -> OK and your file should load. Ghidra will let you know that the file has not been analyzed and will ask if you would like it to be analyzed now. Click Yes -> Analyze. You may get some error messages, but these errors won't prevent you from completing the challenge; click OK. Your screen should now look like this:
Since we know we are looking for a string, we can use Ghidra to search for that data type for us:
We will uncheck "Require Null Termination" to ensure we get the broadest search possible. All other options can be left the same.
Ghidra then provides us with the following output, which includes where in the code we can find these strings. Note that in the far right column, the value for "Is Word" is false:
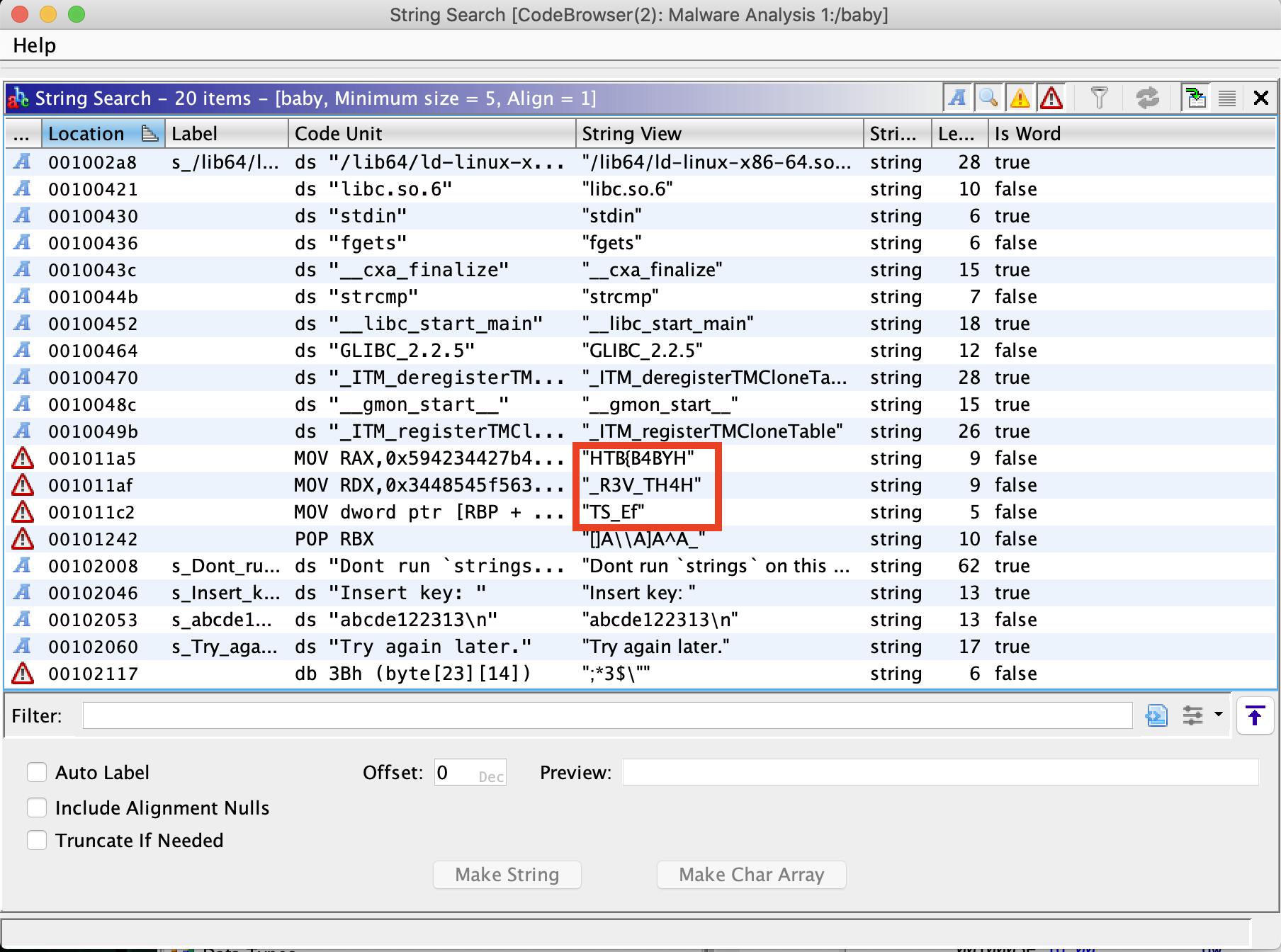
If we highlight the first string containing "HTB{B4BYH", Ghidra will navigate to that section of the code behind the search output window. Going back to the main window, the section of code that's highlighted does not contain ASCII characters.
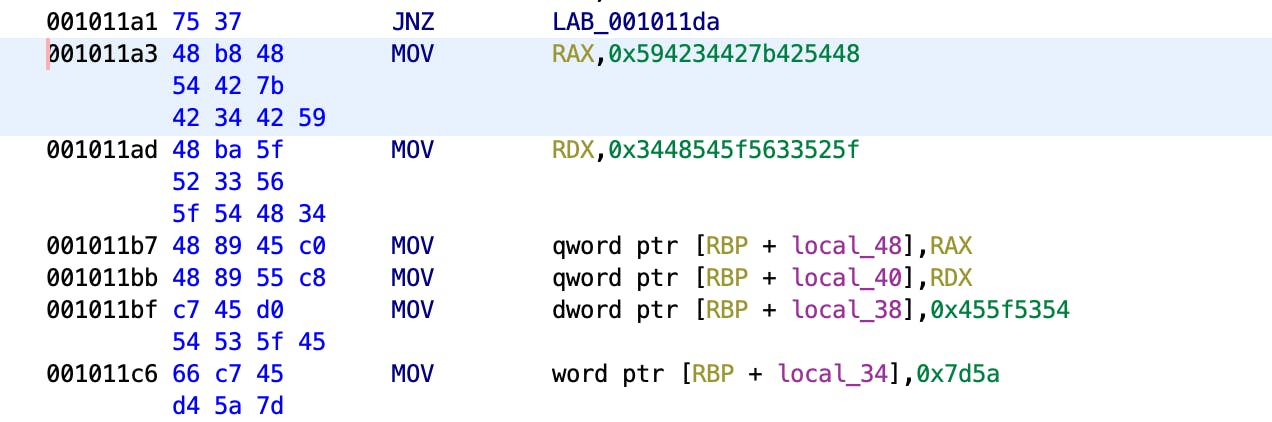
In order to get the human-readable string, we will need to convert the data in that area of the code by right-clicking and selecting "Convert -> Char Sequence". You can already see that in the string starts to show in the "Char Sequence" selection:
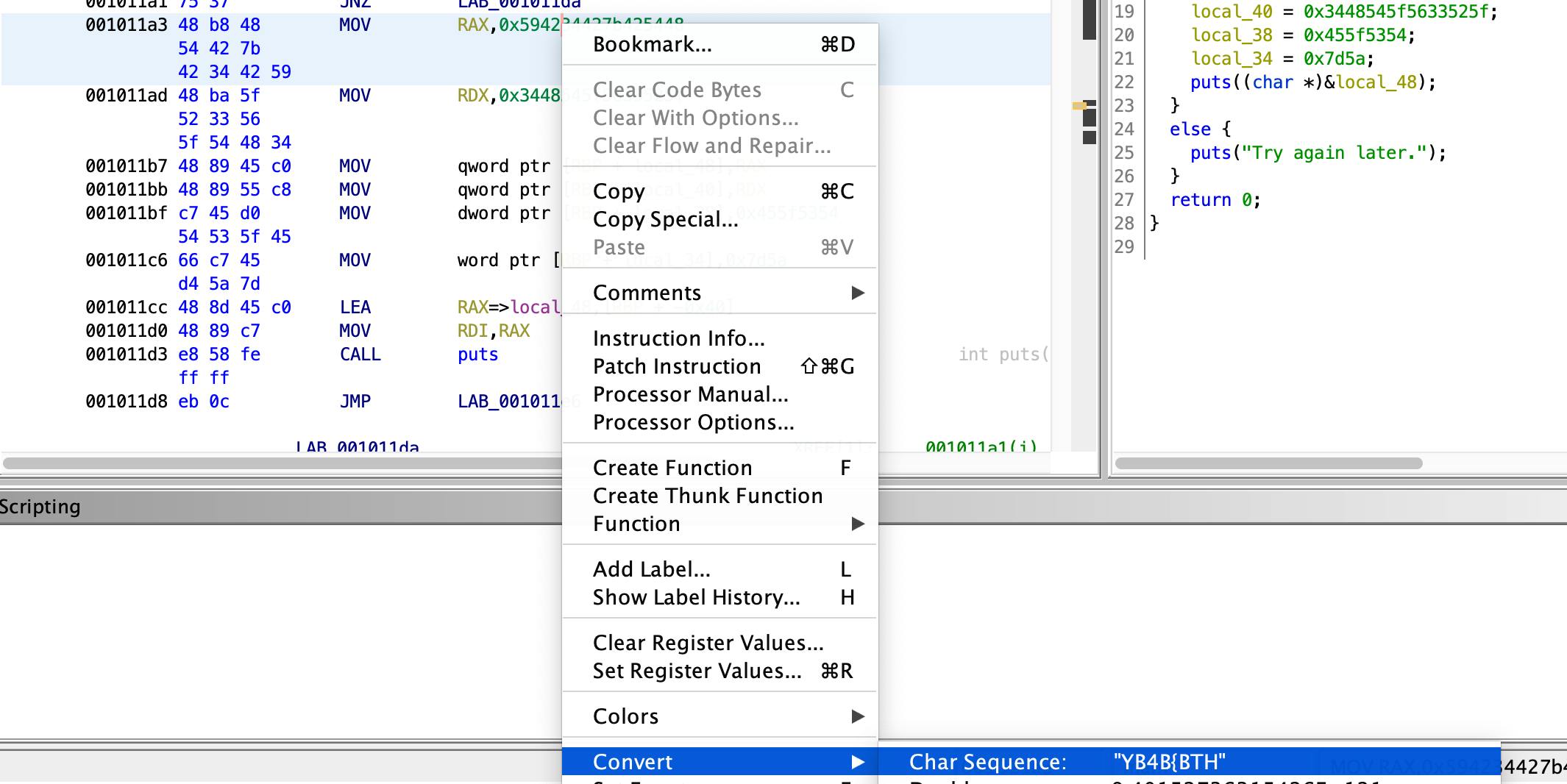
Repeat the above step for the areas of the code below it:
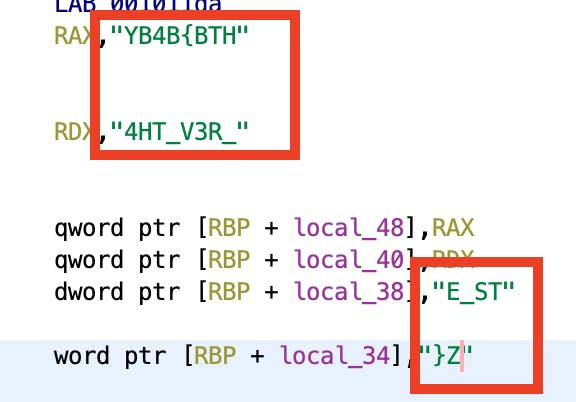
We are left with the following strings:
YB4B{BTH
4HT_V3R_
E_ST
}Z
This output is the flag flipped backwards and in sequential chunks. If we flip the strings across an imaginary Y-axis and concatenate them, we get the flag:
HTB{B4BY_R3V_TH4TS_EZ}
