What is Lsass.exe
The Windows Local Security Authority Subsystem Service, or lsass.exe, is an executable native to all Windows operating systems. It is a core component of Windows OS security and is responsible for the following:
Which users are allowed to log on to the machine
Password policies
Privileges granted to users and groups
System security auditing settings
User authentication
Sending security audit messages to the event log
It can be found in the C:\Windows\system32 directory and interacts with other security system components in the Windows operating system to achieve the objectives listed above. Lsass makes the user's experience efficient by preventing the user from having to constantly re-enter credentials when trying to access network resources, file shares, among other things. It does this by storing active user credentials in memory.
Lsass will store credentials in memory for a very short amount of time after the user logs off (time varies for different operating systems, but the default for Windows 8.1+ is 30 seconds). Alternatively, if the user does not log off, it will keep the credentials cached until the system restarts.
How does credential dumping work?
Credential dumping is the process of retrieving user authentication credentials from memory on a target host. Commonly, more than one set of credentials can be retrieved from a host, allowing the threat actor to then leverage those credentials to access other devices on the network and continue to harvest credentials at an exponential rate if not thwarted. Needless to say, lsass can be a lucrative target for someone trying to gain widespread access to a network.
How do threat actors dump credentials from lsass?
There's a few tools and methods that can be leveraged to harvest credentials from a target system.
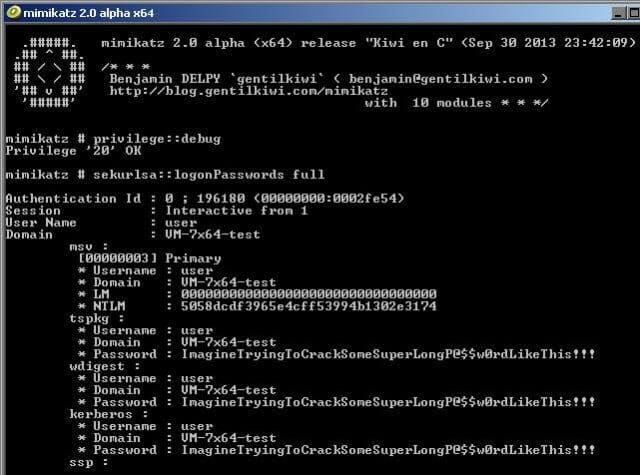
Mimikatz
Possibly one of the most renown pieces of credential-stealing malware is Mimikatz. Developed by a former French government agency worker, the tool is one of the most widely used tools for credential theft.
By running the sekurlsa::logonPasswords command within Mimikatz, threat actors can dump password data stored in lsass memory. More information regarding the tool and it's capabilities can be found here.
Creating a Dump File
While having admin credentials is required for this to work, it affords threat actors the opportunity to dump additional user credentials on the target host. It can be accomplished by running task manager as an administrator, right-clicking on the lsass process, and selecting Create Dump File. A pop-up will then show where the dump file is located. Simple, "noisy," but nonetheless a method (and an effective one) in a poorly monitored environment.
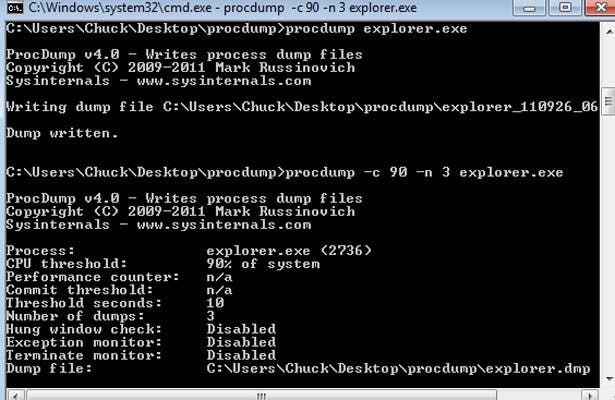
Using ProcDump
ProcDump is a Windows Sysinternals tool intended for application monitoring and generating crash dumps. Lsass is unfortunately not an exception when it comes to using ProcDump; the tool can be pointed at lsass to dump its process memory and therefore harvest credentials from the target system.
Privately-developed tools
Some APTs are sophisticated enough to write their own credential harvesting tools. For example, APT29, also known as COZY BEAR, NOBELIUM, and CozyDukes, developed PinchDuke, which is able to steal credentials from browsers, password stores, and also dump credentials from memory.
You can read more on PinchDuke here.
How to protect against lsass credential dumping
- Patch your systems regularly
- Enable LSA protection: This can be done by setting the value for "RunAsPPL" to "1" under the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
(Microsoft has in-depth detail regarding this setting here.
- Use restricted admin mode: Lsass doesn't only store user credentials from interactive logins; it stores RDP credentials as well. To reduce the risk of admin credentials being compromised, adjust the value for "DisableRestrictedAdmin" to "0" under the following registry key:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa
- Enable restricted admin outbound credentials: This setting does not allow the administrator account to authenticate to a remote system from a system they have RDP'd into. If this setting is disabled, the administrator account can remotely access a system, and then remotely access another device and authenticate using the domain\computer$ of the system they are remotely logged into. Restricting admin outbound credentials prevents the administrator account from daisy-chain-hopping from system to system in the environment, and also protects the admin credentials. To do this, set the value for "DisableRestrictedAdminOutboundCreds" to "0" under the following registry key:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa
More information on the previous two recommendations can be found here.
- User education: I can hear the collective network administrator groan on this one, but it's an important and effective one. Educating users on the importance of logging off of their systems (rather than walking away at the end of the day and letting the system go to sleep) can reduce the amount of credentials at risk should an attacker successfully access their system. Getting users to practice good cyber hygiene is sometimes a steep challenge, but being persistent and active in user education can greatly reduce the adversary attack surface in your organization.
Examples of large-scale attacks where lsass credential dumping was used
Additional Reading